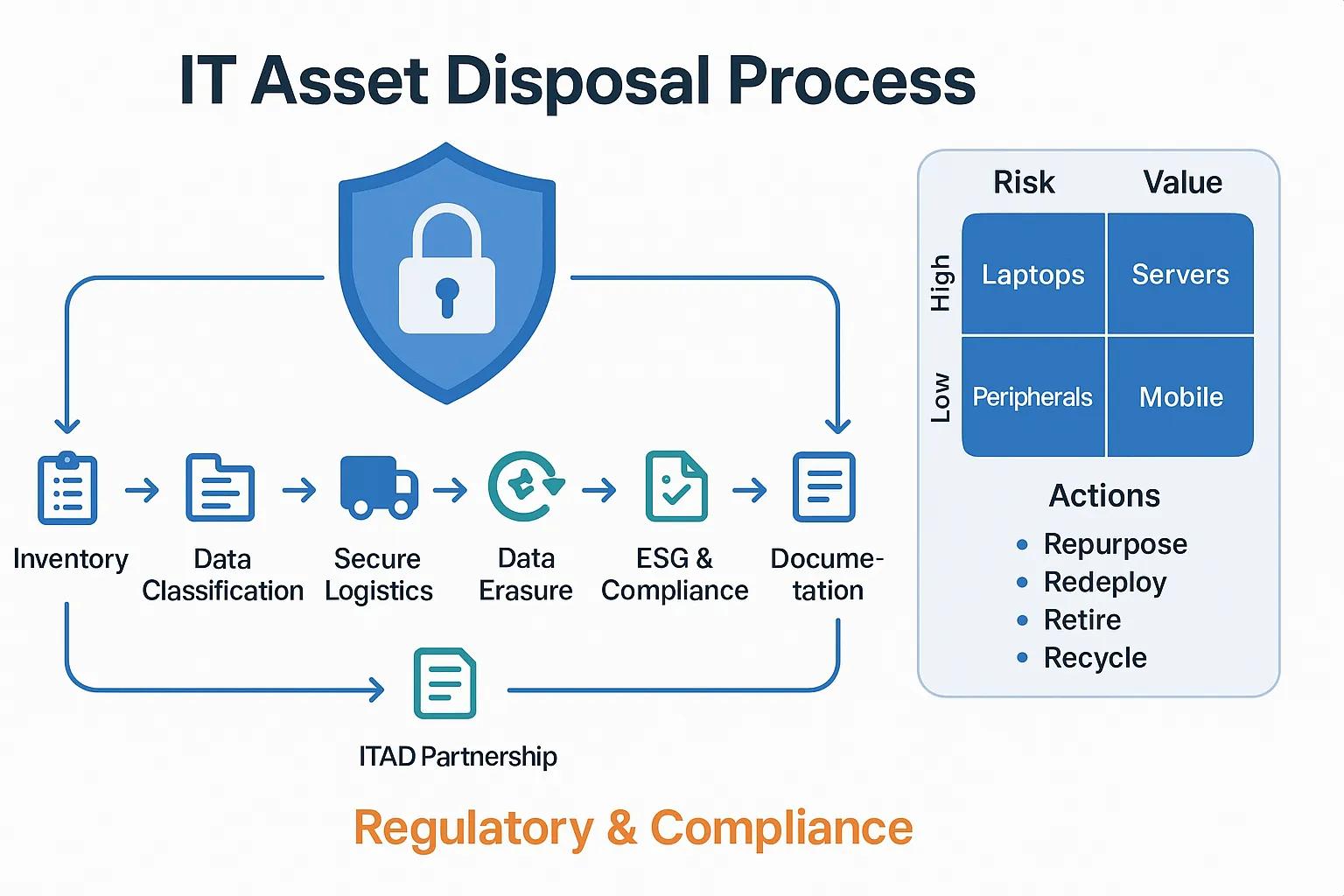
Why IT Asset Disposal Needs a Structured Approach
- Mitigate legal and security risks.
- Align with corporate ESG and sustainability goals.
- Maximise the residual value of redundant assets.
- Create a robust, auditable trail for regulators and stakeholders.
ITAD Risk & Value Matrix
| Asset Type | Data Sensitivity | Resale Potential | Priority Action |
|---|---|---|---|
| Laptops with SSDs | High | High | Certified erasure, resale via trusted partner |
| Servers / Storage | High | Medium | Wipe securely, redeploy or strip for parts |
| Obsolete peripherals | Low | Low | Recycle to WEEE standards |
| Recent mobile devices | Medium | High | Factory reset, resale with IMEI cleared |
1. Create a Complete Asset Inventory
- Device make, model, and serial number
- Asset tag or unique ID
- Specification and configuration
- Ownership or department details
- Condition assessment
- Associated software licences
2. Classify Data Sensitivity and Security Requirements
- High sensitivity: Devices containing personal, financial, or classified information.
- Medium sensitivity: Devices with business data requiring controlled handling.
- Low sensitivity: Devices with minimal or no stored data.
3. Plan Secure Logistics and Chain of Custody
- Vetted, DBS-checked personnel and secure transport
- Tamper-evident containers and barcode tracking
- Collection documentation and detailed manifests
- End-to-end chain of custody reporting
4. Data Erasure or Destruction
- Certified data erasure: Use ADISA-approved software aligned with NIST 800-88 standards.
- Physical destruction: For failed drives or devices unsuitable for reuse, shredding to appropriate particle sizes ensures irretrievability.
5. Maximise Reuse and Resale Opportunities
- Identify assets suitable for refurbishment and redeployment.
- Clear BIOS passwords and MDM locks to protect and enhance resale value.
- Partner with a supplier with strong resale channels across global marketplaces and specialist brokers.
- Share in resale returns to fund sustainability initiatives or reduce project costs.
Understanding IT Asset Value Degradation
Typical Asset Value Degradation Timeline
| Asset Type | Initial Residual Value (Month 0) | After 3 Months | After 6 Months | After 12 Months | Key Considerations |
|---|---|---|---|---|---|
| Business-grade laptops | 100% | 80–85% | 60–70% | 30–40% | High demand; value drops quickly once new models launch. |
| Smartphones & tablets | 100% | 75–80% | 55–65% | 25–35% | Market heavily driven by model cycles and OS support. |
| Servers & storage | 100% | 85–90% | 70–80% | 50–60% | Longer lifecycle but niche resale channels. |
| Monitors & peripherals | 100% | 85% | 70% | 40–50% | Lower resale value; demand declines steadily. |
Why It Matters
- Delays equal lost value – the longer assets sit idle, the less you’ll recover.
- Holding for “later disposal” rarely pays off – missed resale windows are hard to recapture.
- Fast, structured ITAD protects residual value and can help fund future IT refreshes or sustainability initiatives.
6. Ensure Environmental Responsibility
- Is registered with the Environment Agency
- Operates to ISO 14001 standards
- Follows a reuse-first hierarchy, minimising landfill
- Provides environmental impact reporting (e.g. carbon savings, reuse vs recycling metrics)
7. Document and Report Everything
- Asset inventory and classification logs
- Collection and chain of custody documentation
- Certificates of erasure or destruction
- Resale reports and environmental data
Regulatory & Compliance Reference Table (UK)
| Process Step | Relevant Regulation / Standard | Why It Matters |
|---|---|---|
| Data sanitisation | GDPR, NIST 800-88 | Legal obligation to erase data securely |
| Logistics & chain of custody | UK GDPR, ISO 27001 Annex A, ICO guidance | Proves data control pre-processing |
| Environmental disposal | WEEE Regulations, Environment Agency | Ensures legal e-waste management |
| Reporting & audit trail | GDPR Article 30 (ROPA), ICO guidance | Provides evidence during audit or breach investigation |
8. Partner With a Trusted ITAD Provider
- ISO 27001, ISO 9001, ISO 14001 accreditations
- Cyber Essentials certification
- Transparent reporting and client portal access
- Experience with both public and private sector ITAD
- A proven commitment to data security, sustainability, and value recovery