Frequently Asked Questions
How to wipe hard drive?
Wiping a hard drive involves securely erasing all data to prevent recovery. You can do this by using built-in tools like Disk Utility on macOS or Disk Management on Windows, or third-party software designed for secure data deletion.
What is data shredding method?
The data shredding method is a secure process used to permanently erase data from storage devices by overwriting it multiple times, making recovery virtually impossible. This ensures sensitive information is irretrievable and protects against data breaches.
What are UK IT disposal laws?
UK IT disposal laws govern the safe and responsible disposal of electronic waste, ensuring that data protection and environmental regulations are met. These laws require businesses to securely dispose of IT assets to prevent data breaches and minimize ecological impact.
How to destroy SSD data?
The process of destroying SSD data involves using secure erasure methods such as software-based overwriting tools, which comply with data sanitisation standards, or physically destroying the drive to ensure that data cannot be recovered.
What is IT asset destruction UK?
IT asset destruction in the UK refers to the secure and environmentally responsible process of disposing of outdated or unwanted IT equipment, ensuring that sensitive data is irretrievably destroyed in compliance with legal and regulatory standards.
What methods ensure complete hard drive wiping?
The methods that ensure complete hard drive wiping include using data destruction software that complies with industry standards, physical destruction of the drive, and multiple overwriting techniques to eliminate all data traces effectively.
How effective is data shredding for security?
The effectiveness of data shredding for security is significant, as it permanently destroys sensitive information, making recovery virtually impossible and thereby protecting against data breaches and unauthorized access.
What are the steps for SSD data destruction?
The steps for SSD data destruction include securely erasing data using software tools that comply with industry standards, physically destroying the SSD if necessary, and verifying the effectiveness of the destruction process to ensure data cannot be recovered.
What regulations govern IT asset disposal in the UK?
The regulations governing IT asset disposal in the UK include the Waste Electrical and Electronic Equipment (WEEE) Directive, the Data Protection Act, and the Environmental Protection Act, all aimed at ensuring safe and responsible disposal practices.
How can I verify hard drive data wiping?
Verifying hard drive data wiping involves using software tools that can confirm the data has been irretrievably erased. Additionally, conducting a physical inspection or employing a forensic analysis can provide further assurance that the data is no longer accessible.
What is the best practice for data shredding?
The best practice for data shredding involves using certified shredding services that comply with industry standards, ensuring complete destruction of data on physical media to prevent unauthorized access and protect sensitive information.
How to ensure compliance with UK disposal laws?
Ensuring compliance with UK disposal laws involves adhering to regulations regarding the safe and environmentally responsible disposal of IT assets. This includes following guidelines set by the Environment Agency and obtaining necessary certifications for waste disposal.
What tools are used for hard drive wiping?
The tools used for hard drive wiping include software solutions like Blancco or Ziperase, as well as hardware tools such as degaussers and physical destruction methods to ensure data is irretrievable.
What are the risks of improper data destruction?
The risks of improper data destruction include potential data breaches, legal penalties, and damage to a company’s reputation. Sensitive information can be exposed, leading to financial loss and a loss of customer trust.
How to choose a data shredding service?
Choosing a data shredding service involves evaluating their security measures, certifications, and compliance with regulations. Look for a provider that offers transparent processes, reliable customer support, and environmentally responsible disposal methods to ensure your data is handled safely.
What is the process for IT asset destruction?
The process for IT asset destruction involves securely wiping data, physically destroying the devices, and providing certification of destruction to ensure compliance with regulations. This ensures that sensitive information is irretrievable and environmentally disposed of responsibly.
How often should data shredding be performed?
Data shredding should be performed regularly, ideally whenever sensitive data is no longer needed, or at least annually, to ensure compliance with security standards and to protect against data breaches.
What are the consequences of data breaches?
The consequences of data breaches are significant and can include financial losses, legal penalties, reputational damage, and loss of customer trust, leading to long-term impacts on a business's operations and growth.
How to securely dispose of old IT equipment?
Secure disposal of old IT equipment involves using certified e-waste recycling services that ensure data destruction and environmentally friendly practices, safeguarding sensitive information while complying with regulations.
What certifications should a data destruction service have?
Data destruction services should have certifications such as NAID (National Association for Information Destruction) or ISO 27001, ensuring compliance with industry standards for secure data handling and disposal practices.
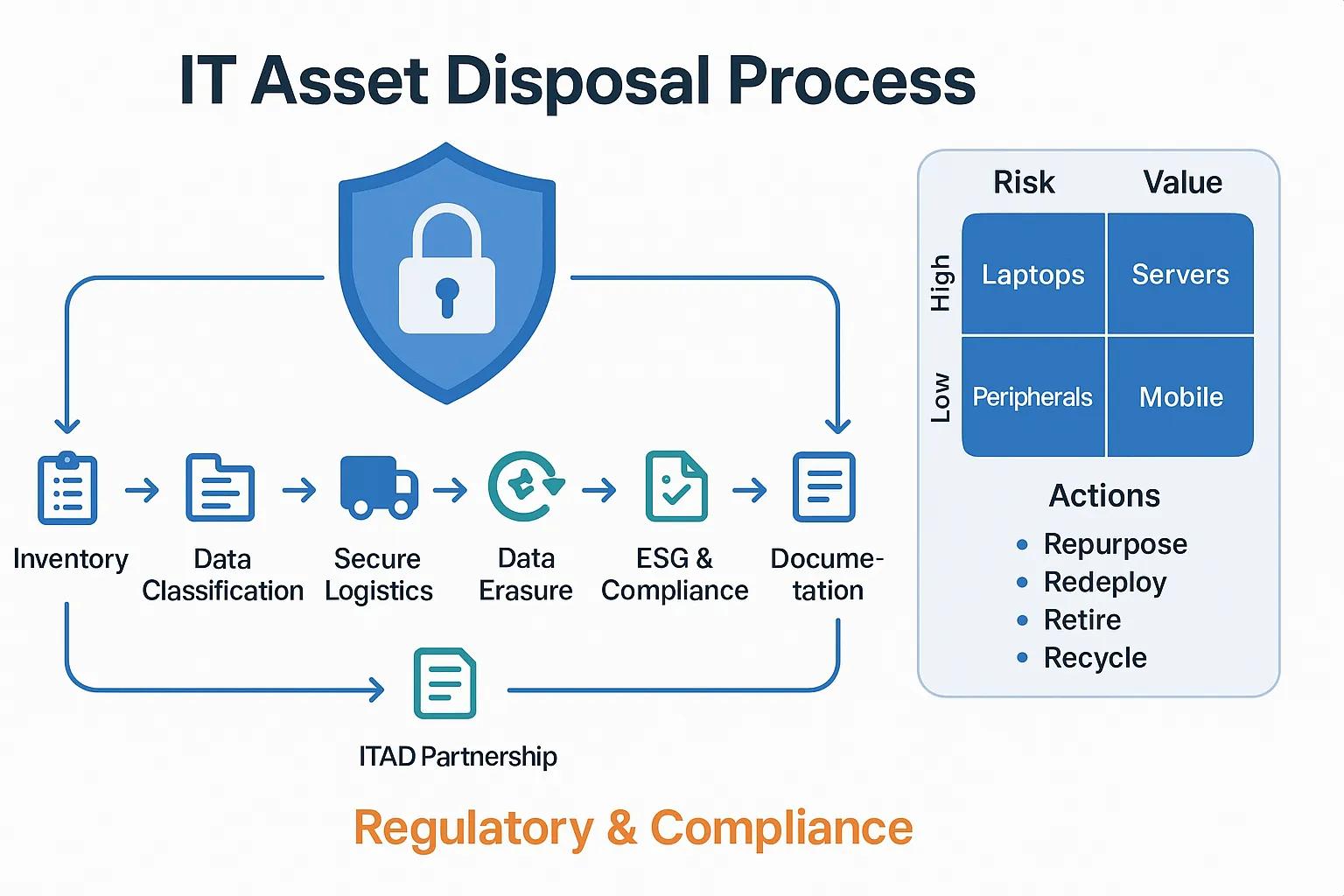
How to document IT asset disposal processes?
Documenting IT asset disposal processes involves creating clear, step-by-step procedures that outline asset identification, data wiping, recycling, and disposal methods. Ensure compliance with relevant regulations and maintain records of each disposal for accountability and traceability.
What is the difference between wiping and shredding?
The difference between wiping and shredding lies in their methods of data destruction. Wiping involves overwriting data on a storage device to make it unrecoverable, while shredding physically destroys the device itself, ensuring that data cannot be retrieved.
How to assess the effectiveness of data destruction?
Assessing the effectiveness of data destruction involves verifying that all data has been irretrievably erased through methods such as third-party audits, certification of destruction, and compliance with industry standards to ensure complete data security.
What are common misconceptions about data shredding?
Common misconceptions about data shredding include the belief that physical destruction alone guarantees data security and that all shredding services are equally effective. In reality, proper shredding requires adherence to industry standards and certifications to ensure complete data protection.
How to handle sensitive data during disposal?
Handling sensitive data during disposal involves ensuring that all data is securely erased or destroyed to prevent unauthorized access. Employing certified data destruction services and following industry best practices is essential for maintaining data security and compliance.
What technologies aid in secure data destruction?
Technologies that aid in secure data destruction include data wiping software, degaussers, and physical destruction methods such as shredding or crushing hard drives. These solutions ensure that sensitive information is irretrievably erased, protecting against data breaches.
How to train staff on data disposal policies?
Training staff on data disposal policies involves providing clear guidelines, conducting regular workshops, and utilizing engaging materials to ensure understanding of secure disposal methods and compliance with regulations. Regular assessments can reinforce knowledge and practices.
What is the lifespan of data on a hard drive?
The lifespan of data on a hard drive can vary significantly, typically lasting between 3 to 5 years under normal usage conditions, but factors like environmental conditions and usage patterns can affect data integrity over time.
How to recover data from a wiped hard drive?
Recovering data from a wiped hard drive involves using data recovery software that can scan the drive for remnants of deleted files. If the data has been overwritten, professional data recovery services may be necessary for successful retrieval.
What are the environmental impacts of IT disposal?
The environmental impacts of IT disposal include the release of hazardous materials, such as heavy metals and toxins, into the ecosystem, which can contaminate soil and water. Proper disposal and recycling are essential to mitigate these effects and promote sustainability.